| Download: | sigtrace.pl |
| signed.db.gz (4/21/02) | |
| keynames.db.gz (7/25/01?) (optional) (just the primary cluster) |
sigtrace.pl traces a signature path through a keyring. It currently requires signed.db.gz(4/21/02) which is a precompiled table containing all signature relationships on the keyring servers, under 3mb compressed, and must be gunzipped. If you have keynames.db.gz (7/25/01?), it will also display the names and email addresses of people in the path (this only includes those in the largest signature cluster).
I also created a wrapper (mutt-sigtrace) to display paths to keys that signed emails within the mailreader mutt.
An example, tracing a signature path from the creator of PGP to myself:
$ /usr/bin/time ./sigtrace.pl FAEBD5FC 0E9FF879 Data loaded, tracing.... level:0 keys:1 seconds:0 level:1 keys:76 seconds:0 level:2 keys:826 seconds:0 level:3 keys:2 seconds:0 4 hop path: FAEBD5FC 9D496584 F6F83318 80675E65 0E9FF879 FAEBD5FC Philip R. Zimmermann <prz@pgp.com> 9D496584 Network Associates TNS Division Employee Certification Key F6F83318 Jason Bobier <jason@prismatix.com> 80675E65 Leonard D. Rosenthol <leonardr@lazerware.com> 0E9FF879 Darxus <Darxus@ChaosReigns.com> 0.29user 0.02system 0:00.31elapsed 99%CPU (0avgtext+0avgdata 0maxresident)k 0inputs+0outputs (352major+1260minor)pagefaults 0swaps0.31 seconds on an athlon 1.4ghz. 6.19 seconds on a p2 233.
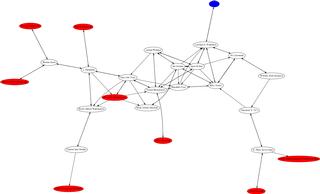
If you feed all of the keys in the paths between several people to sig2dot, you get a pretty graph of all the relationships.
4/21/02
Mother keyring is 1.8gb, contains 1,639,400 keys, and 3,749,048 signatures.
Tracing all (168,003) possible signature paths from myself takes 4.81 seconds
on a 1.4ghz athlon.
7/25/01
The mother keyring, served by the keyserver
network, is about 1.6gb, and contains 1,467,201 keys, and 3,311,896
signatures. After parsing the signature relationships to a tied hash (thanks to mct), and making more use of hashes, it now
takes 18 seconds to trace every possible path from myself on a p2 233. Hashes
rock.
keynames.db took 14.32 hours to generate.
11/26/00
Keyring size: 1.4gb
1,279,224 keys, and 2,837,692 signatures.
The code to parse the signatures from stdin is still present, but commented out. I will be adding flags to allow signature data to be parsed directly from stdin, or to build a .db from data from stdin.
Famous Keys (you might want to try tracing to/from)
pub 1024D/57548DCD 1998-07-07 Werner Koch (gnupg sig) <dd9jn@gnu.org> pub 1024D/148C6F43 1997-10-16 Steve Wozniak <steve@woz.org> pub 1024D/449FA3AB 1999-10-05 Linus Torvalds <torvalds@transmeta.com> pub 1024D/2FA3BC2D 1998-07-05 Wichert Akkerman <wakkerma@debian.org> pub 1024D/517D0F0E 2000-10-10 Linux Kernel Archives Verification Key <ftpadmin@kernel.org> pub 1024D/8421F11C 1997-10-05 Eric S. Raymond <esr@thyrsus.com> pub 1024D/FAEBD5FC 1997-04-07 Philip R. Zimmermann <prz@pgp.com> pub 1024R/20B19259 2000-09-20 CERT Coordination Center <cert@cert.org>If you know of other keys worth tracing from/to, please email me.
Want to swap signatures with me ?
If you are in, or expect to be in, the Philadelphia Pennsylvania area, and would like to swap signatures, email me, I'd be happy to meet you somewhere. The best time/place would probably be a Linux user group meeting. Bring photo ID matching the name on your key, and a verified copy of your fingerprint.
On a 1.4ghz athlon with 512mb ddr ram, with the 7/25/01 dataset:
gpg --no-default-keyring --keyring ./pubring.pgp --fast-list-mode
--list-sigs > pubring.sigs
took 3:26:42.
cat pubring.sigs | ./sigtrace.pl 09AC0A6A 0E9FF879
took 1:08.
The following commandline is here only for reference and ammusement. Do not be afraid.
gpg --keyserver wwwkeys.pgp.net --no-default-keyring --keyring darxus.famous.gpg --recv-keys `echo 0E9FF879 20B19259 57548DCD 0E9FF879 148C6F43 0E9FF879 449FA3AB 0E9FF879 2FA3BC2D 0E9FF879 0E9FF879 517D0F0E 8421F11C 0E9FF879 C7A966DD 0E9FF879| xargs -n 2 ./sigtrace.pl | grep "hop path" | cut -d':' -f2 | tr " " "\012 " | sort -u | tr "\012" " "` ; gpg --no-default-keyring --keyring darxus.famous.gpg --list-sigs | ./sig2dot.pl > darxus.famous.dot ; neato -Tps -Gsplines=true -Gsep=.1 darxus.famous.dot > darxus.famous.ps ; convert darxus.famous.ps darxus.famous.jpg
Comment on this page.
Return to Darxus' Home Page
Thu Dec 19 14:52:55 EST 2002
Valid HTML 3.2.